1Komos Identity Verification & Wallet
1Komos Identity Verification
& Wallet
1Kosmos enables remote identity verification and passwordless multi-factor authentication for workers, customers and residents to securely transact with digital services.
I led the re-designing a streamlined, user-friendly dashboard and verification flow for managing identity documents and enhancing user security.
1Kosmos enables remote identity verification and passwordless multi-factor authentication for workers, customers and residents to securely transact with digital services.
I led the re-designing a streamlined, user-friendly dashboard and verification flow for managing identity documents and enhancing user security.

Company
1Kosmos
Lead Designer
Role
UX Strategy,
Design, Research
Contribution
Figma, Illustrator,
Lottie files, FigJam
Tools Used
Project Overview
Product Defination
Product Defination
What does it do?
What does it do?
1Kosmos provides a digital identity verification platform that focuses on secure, seamless, and passwordless authentication for users. It enables individuals and organizations to securely manage and verify identities using a combination of biometric authentication (Live ID), document verification (e.g., SSN, driver’s license, passport), and advanced encryption.
1Kosmos manages more than 50 million identities on its BlockID
1Kosmos provides a digital identity verification platform that focuses on secure, seamless, and passwordless authentication for users. It enables individuals and organizations to securely manage and verify identities using a combination of biometric authentication (Live ID), document verification (e.g., SSN, driver’s license, passport), and advanced encryption.
1Kosmos manages more than 50 million identities on its BlockID
The Problem
The Problem
1Kosmos was already providing identity verification solutions, but the existing system had limitations in usability and scalability. Users, especially in high-security environments like government verification or financial services, often encountered complex login and document upload processes. These difficulties increased user frustration.
As the market for secure passwordless authentication and biometric verification expanded, 1Kosmos recognized the need for a platform overhaul. The system needed to streamline identity verification processes and ensure the uniqueness of users while complying with government regulations (IAL1, IAL2).
1Kosmos was already providing identity verification solutions, but the existing system had limitations in usability and scalability. Users, especially in high-security environments like government verification or financial services, often encountered complex login and document upload processes. These difficulties increased user frustration.
As the market for secure passwordless authentication and biometric verification expanded, 1Kosmos recognized the need for a platform overhaul. The system needed to streamline identity verification processes and ensure the uniqueness of users while complying with government regulations (IAL1, IAL2).
Manual and inefficient identity verification processes at 1Kosmos were limiting their platform's scalability, security and seamless authentication. This highlighted the need for a more streamlined solution to enhance user uniqueness, compliance with security certifications, and overall platform growth.
Manual and inefficient identity verification processes at 1Kosmos were limiting their platform's scalability, security and seamless authentication. This highlighted the need for a more streamlined solution to enhance user uniqueness, compliance with security certifications, and overall platform growth.
Manual and inefficient identity verification processes at 1Kosmos were limiting their platform's scalability, security and seamless authentication. This highlighted the need for a more streamlined solution to enhance user uniqueness, compliance with security certifications, and overall platform growth.
Goal
01
01
Redesigned the 1Kosmos verification + Wallet with a focus to increase user experience and have safe and secure user verification.
Redesigned the 1Kosmos verification + Wallet with a focus to increase user experience and have safe and secure user verification.
02
02
Ensured user uniqueness by verifying identities and gaining user trust through methods like SSN and bank verification, achieving compliance with IAL1 and IAL2 certifications.
Ensured user uniqueness by verifying identities and gaining user trust through methods like SSN and bank verification, achieving compliance with IAL1 and IAL2 certifications.
03
03
Integrated cutting-edge technology to create a frictionless, secure, and user-friendly Identity Wallet prioritizing both security and ease of use.
Integrated cutting-edge technology to create a frictionless, secure, and user-friendly Identity Wallet prioritizing both security and ease of use.
Redesigning the Platform
Challenges
01
01
Multi device verification option.
Multi device verification option.
02
02
Strict compliance with IAL1 and IAL2 certifications.
Strict compliance with IAL1 and IAL2 certifications.
03
03
Verifying user identity is a multi-step process, but the goal was to reduce the number of steps required to create an account and ensure no dropouts occurred.
Verifying user identity is a multi-step process, but the goal was to reduce the number of steps required to create an account and ensure no dropouts occurred.
04
04
04
Asking users to provide sensitive personal information (SSN, passport, and bank details). Users needed to feel confident that their data was secure and being used only for necessary verification purposes.
Asking users to provide sensitive personal information (SSN, passport, and bank details). Users needed to feel confident that their data was secure and being used only for necessary verification purposes.
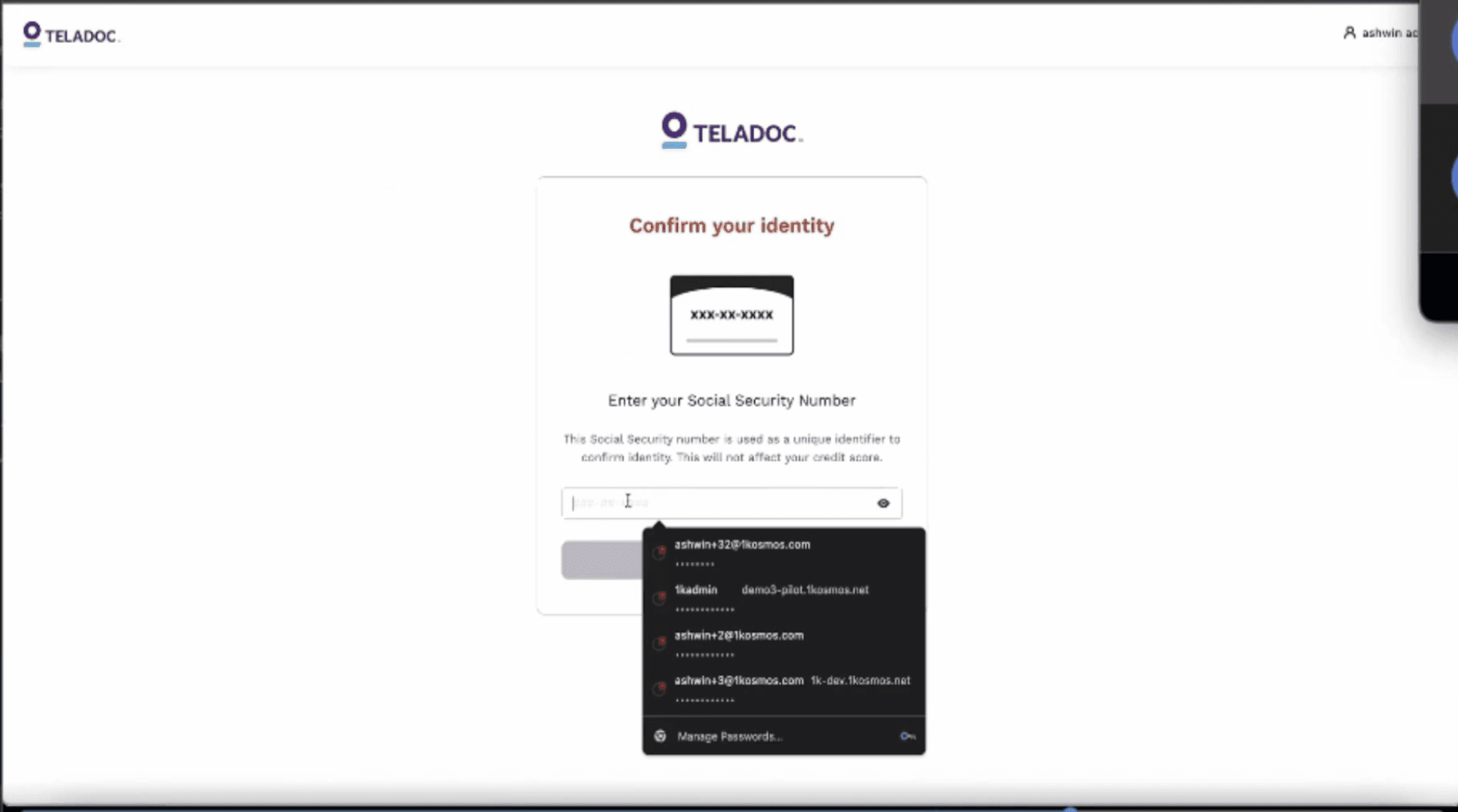

Before
Contextual help on every page of the process, offering tooltips or FAQs related to the specific step the user was on.

Contextual help on every page of the process, offering tooltips or FAQs related to the specific step the user was on.
Progress bar throughout the user journey to give users clear visibility into where they are in the verification process and how many steps are left.
Progress bar throughout the user journey to give users clear visibility into where they are in the verification process and how many steps are left.
Brief, clear explanation of why specific information was being requested.
Brief, clear explanation of why specific information was being requested.
Contextual help on every page of the process, offering tooltips or FAQs related to the specific step the user was on.
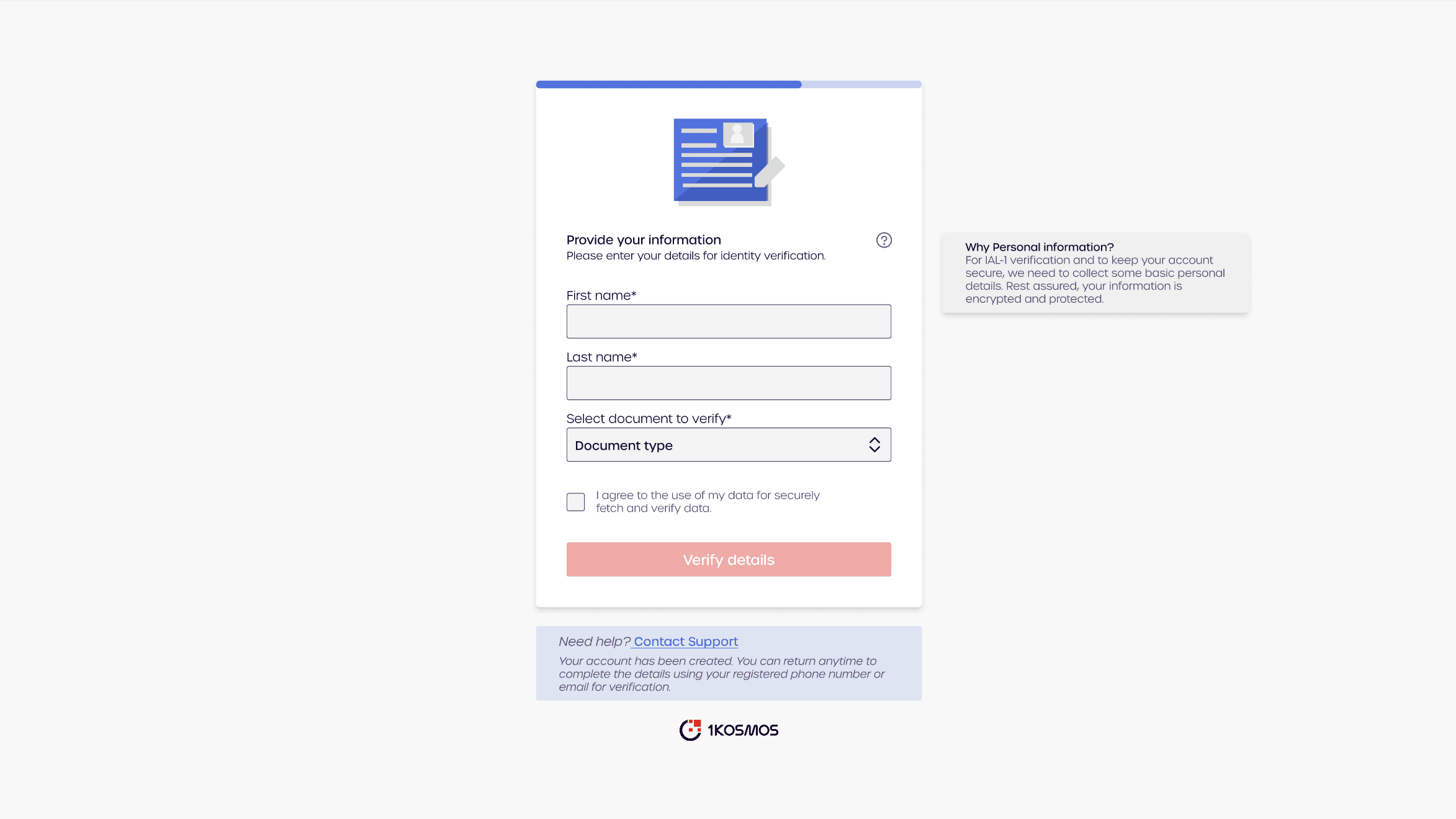
After
After
Contextual help on every page of the process, offering tooltips or FAQs related to the specific step the user was on.
Progress bar throughout the user journey to give users clear visibility into where they are in the verification process and how many steps are left.
Product User flow
Information architecture
Information architecture
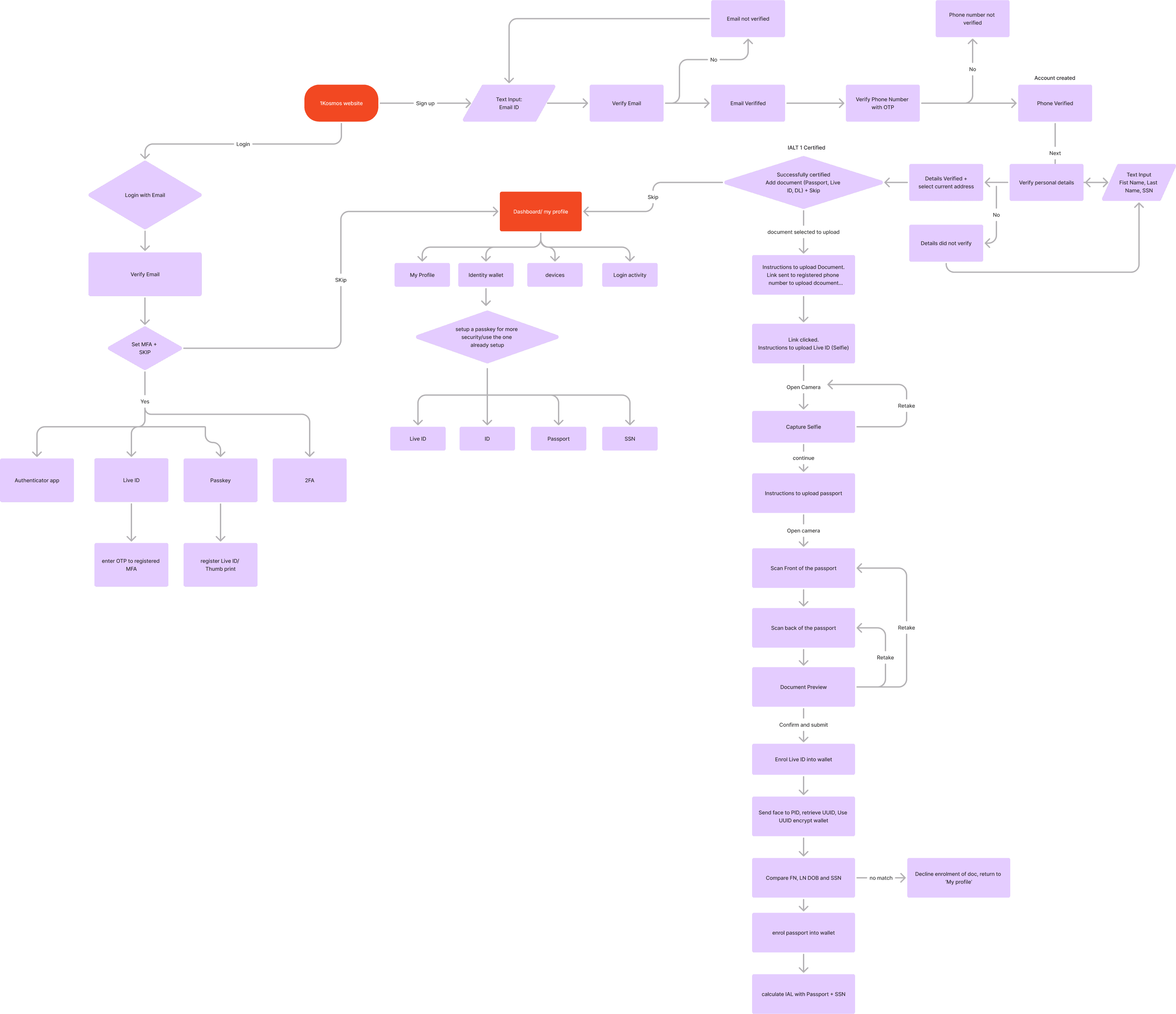



Redesigning the Platform
Approach
Research Phase: Exploring Passwordless Login Systems.
Goal: To identify the best passwordless authentication solutions that balance security and ease of use.
User Uniqueness
Login with email
Login with Phone number
Govt ID
Third party authenticator
Secure Authentication
Password-less Login/Signup
MFA
Biometric
Account Retrieval
Email/Phone recovery
Id verification for recovery
Security Question
Key Features
Key Features
User uniqueness
Use of government-issued IDs (SSN and Bank Account) as a core component of the verification process.
Use of government-issued IDs (SSN and Bank Account) as a core component of the verification process.
Secure Authentication
Email-based login to authenticate users with intigrated phone number recovery as a secondary verification method.
Email-based login to authenticate users with intigrated phone number recovery as a secondary verification method.
Streamlining Account Retrieval
Leveraging email login and phone-based verification, the platform streamlines account recovery.
Leveraging email login and phone-based verification, the platform streamlines account recovery.
Design Implementation
Design Implementation
Transparent messaging throughout the process, explaining how each step contributes to verifying their identity and ensuring their security. Clear, concise language was critical in maintaining trust while complying with regulations.
Transparent messaging throughout the process, explaining how each step contributes to verifying their identity and ensuring their security. Clear, concise language was critical in maintaining trust while complying with regulations.
Progress bar and real-time feedback to guide users through the flow, reducing confusion and preventing dropouts.
Progress bar and real-time feedback to guide users through the flow, reducing confusion and preventing dropouts.
Incorporated data transparency, where users were informed of why their personal data was needed, how it would be used, and what security measures were in place to protect it.
Incorporated data transparency, where users were informed of why their personal data was needed, how it would be used, and what security measures were in place to protect it.
Transparent messaging throughout the process
Transparent messaging
throughout the process
Progress bar
Informed of why their personal data was needed
Informed of why their personal
data was needed
Incorporated data transparency
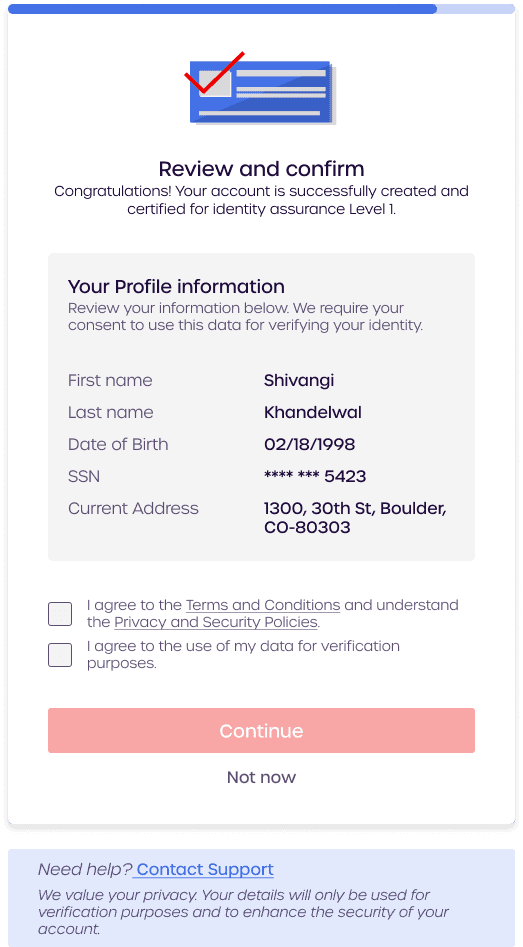
Final Design
Building a Design Language
Building a Design Language
Followed principles to achieve Simplicity, Transparency, Consistency & Security
Simplicity
This includes minimalistic layouts, clear visual hierarchy.
This includes minimalistic layouts, clear visual hierarchy.
Transparency
Users are clearly informed about the what and why, how it will be used, and the security measures in place to protect their data.
Users are clearly informed about the what and why, how it will be used, and the security measures in place to protect their data.
Consistency
Tone of messaging, and interaction patterns are consistent across the platform helped create a unified experience.
Tone of messaging, and interaction patterns are consistent across the platform helped create a unified experience.
Security
Visual cues that reassure users about the platform's trustworthiness. ex(Security icons, end-to-end encryption badges, color-coding for security levels).
Visual cues that reassure users about the platform's trustworthiness. ex(Security icons, end-to-end encryption badges, color-coding for security levels).
Color Palette
#1E0A3C
#EE0000
#72BF75
#4571E6
#F4F4F4
#E3EAFC
Icon formation
+
=
*
*
*
*
*
*
Font Type: Urbane
Urbane | Medium 20px | Main Heading 1
Urbane | Medium 18px | Main Heading 2
Urbane | Medium 16px | Main Heading 3
Urbane | Light 16px | Heading 1
Urbane | Light 14px | Heading 2
Urbane | Italic Light 14px | Instruction 1
Urbane | Italic Light 12px | Instruction 2
Urbane | Italic Light 12px | Error 1
Urbane | Italic Light 10px | Error 2
Final Screens
Final Screens
1Kosmos Dashboard
Wallet securely stores verified identity documents and allows users to easily reuse them across multiple services.
The dashboard offers a clear, easy-to-use interface to access to their data, with the option to revoke permissions or delete data from the system entirely.
Login activity ensures unauthorized access.
Secure their account by logging out of all devices or enabling Multi-Factor Authentication (MFA).
Login to Govt Id verification
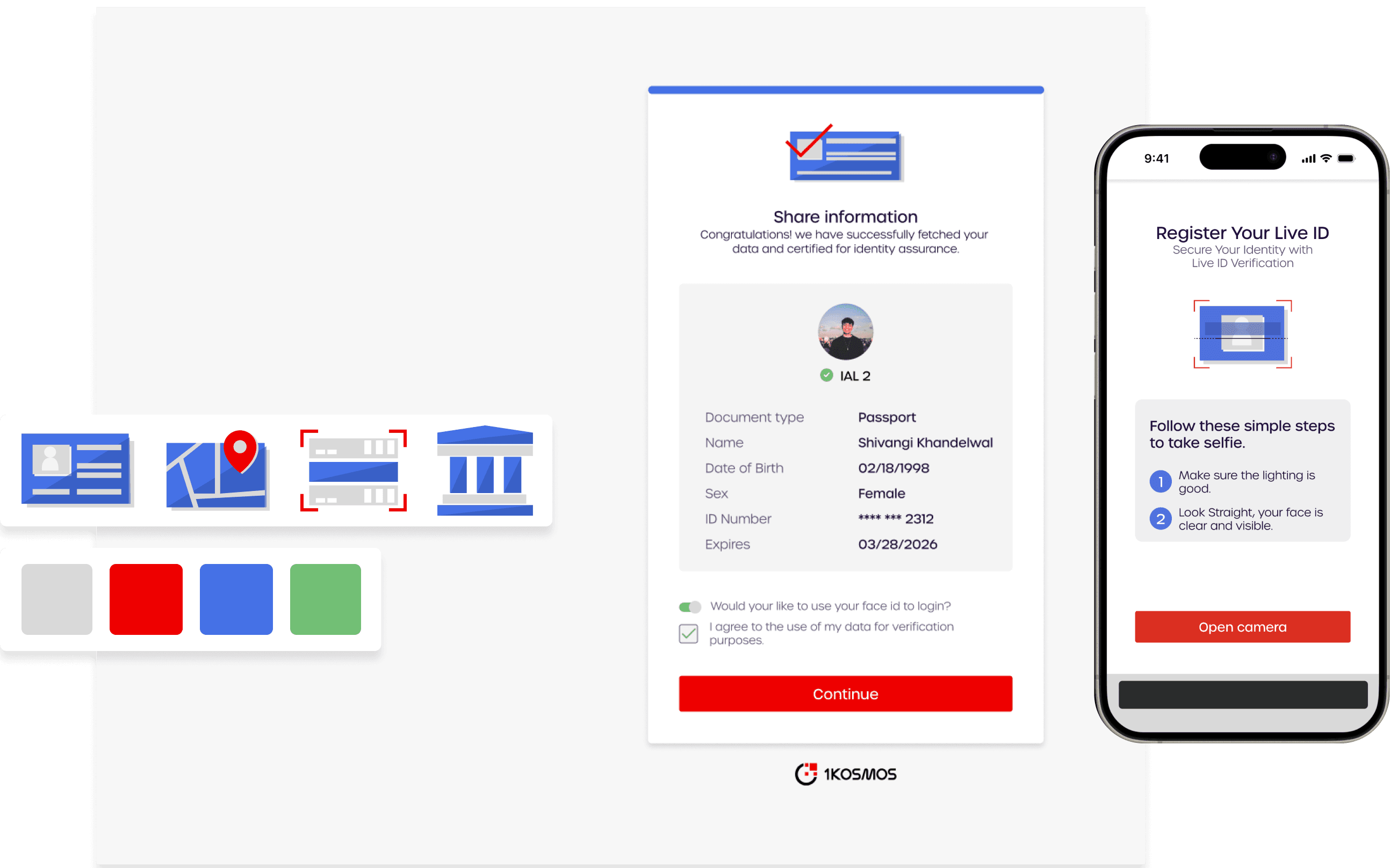
Reduce friction by using passwordless login and allowing users to quickly verify their identity. Insure security through the use of government-issued ID for verification.
Transparency through real-time feedback and progress indicators
Reduce friction by using passwordless login and allowing users to quickly verify their identity. Insure security through the use of government-issued ID for verification.
Transparency through real-time feedback and progress indicators
Data sharing and verification with service provider
Clear, concise instructions at each step make it easy to understand what is required and why.
Immediate validation ensures a smooth experience with minimal frustration, helping users quickly resolve any issues during document upload or Live ID scanning.
Through transparent messaging and secure processes, users feel confident that their personal information and biometric data are being handled securely.
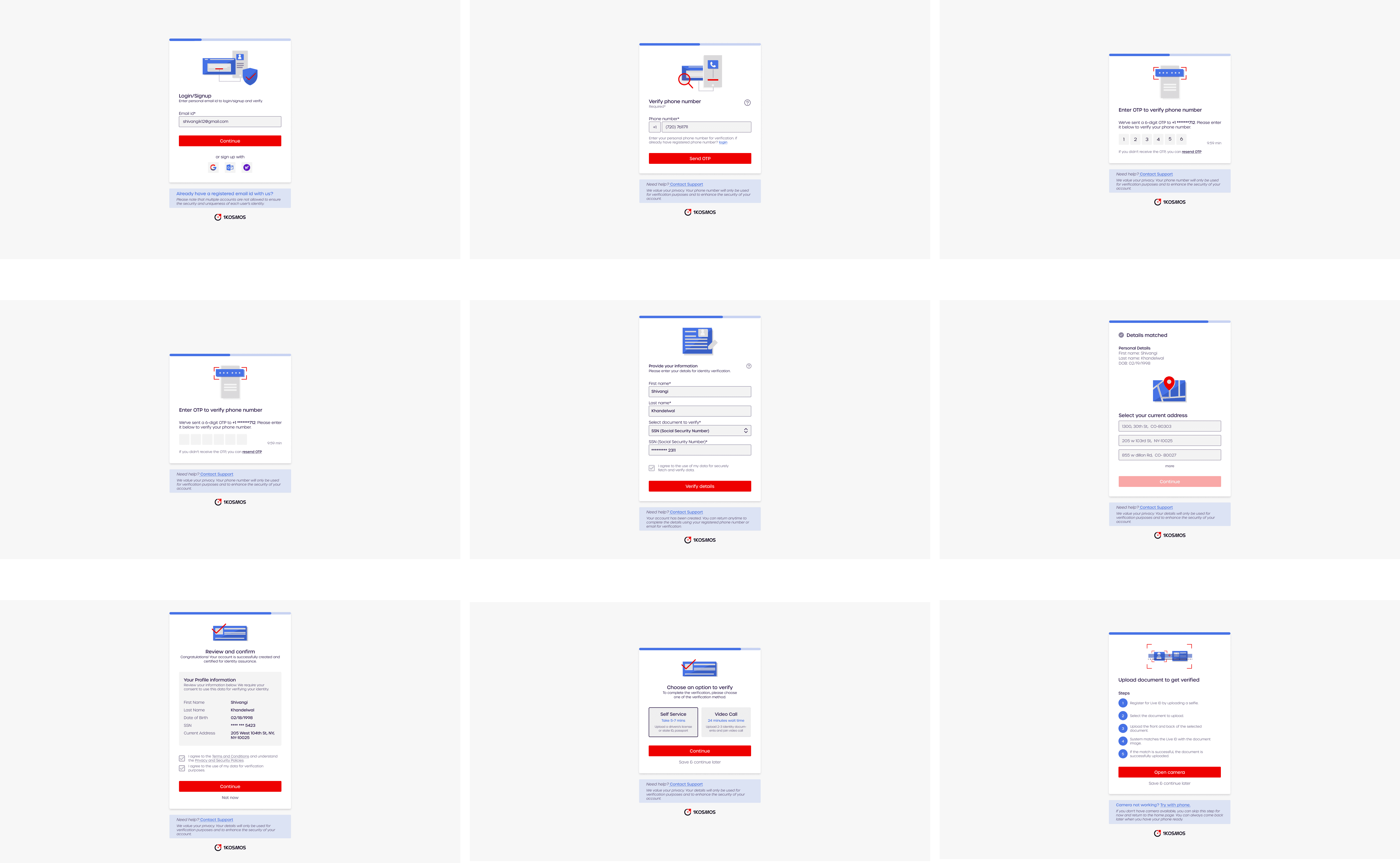


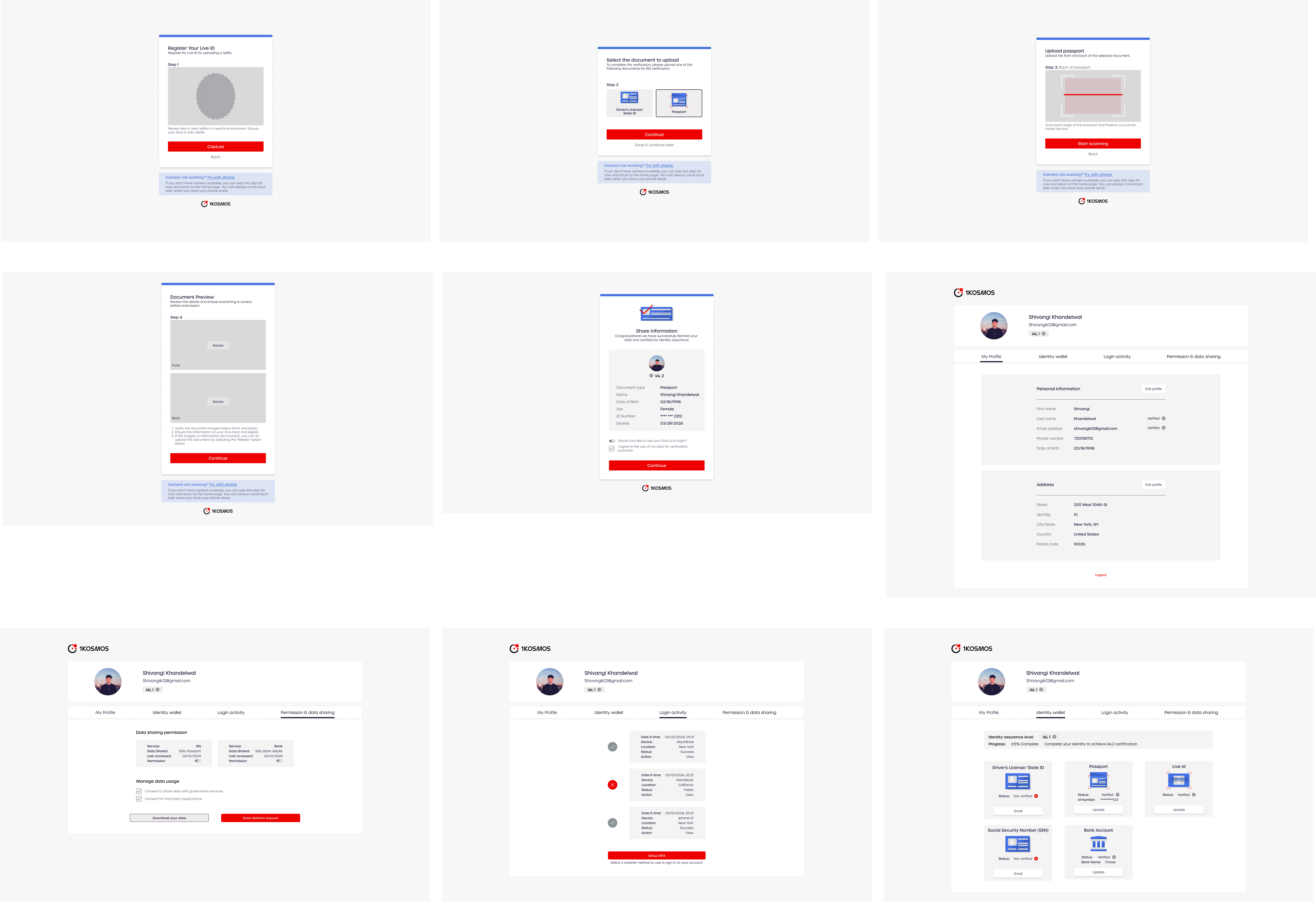


Personal Takeaways
Balancing high-level security protocols with a seamless user experience. Designing around government compliance standards like IAL1 and IAL2 without making the process feel cumbersome
Balancing high-level security protocols with a seamless user experience. Designing around government compliance standards like IAL1 and IAL2 without making the process feel cumbersome
Reinforced my belief that transparency is key in digital products, especially those dealing with personal and sensitive information.
Reinforced my belief that transparency is key in digital products, especially those dealing with personal and sensitive information.
I gained a much deeper understanding of identity management systems, from document verification to biometric authentication.
I gained a much deeper understanding of identity management systems, from document verification to biometric authentication.
Testing different flows of identity verification (e.g., SSN, bank details, biometrics) to refining the Identity Wallet and login systems, each iteration brought new insights that enhanced the user experience.
Testing different flows of identity verification (e.g., SSN, bank details, biometrics) to refining the Identity Wallet and login systems, each iteration brought new insights that enhanced the user experience.
